The Computing Community Consortium (CCC) recently released the Leadership in Embedded Security workshop report. The workshop was organized by former CCC Council Member Kevin Fu (University of Michigan), Wayne Burleson (UMass Amherst), and Farinaz Koushanfar (UC, San Diego). It brought together around fifty academics, industrial researchers, and government agency program managers who work close to the topic of embedded security. The workshop included deep dive group discussions as well as short visionary talks by several international speakers to lend perspectives on successful strategies for funding embedded security research overseas.
The report, titled Grand Challenges for Embedded Security Research in a Connected World, focuses on the challenges and potential research opportunities across five major areas of embedded security:
- Medical and health devices,
- Drones and transportation,
- Smart homes,
- Industry and supply-chain,
- And the smart grid and critical infrastructure.
“Embedded security in connected devices presents challenges that require a broad look at the overall systems design, including human and societal dimensions as well as technical. Particular issues related to embedded security are a subset of the overall security of the application areas, which must also balance other design criteria such as cost, power, reliability, usability and function. Recent trends are converging to make the security of embedded systems an increasingly important and difficult objective, requiring new trans-disciplinary approaches to solve problems on a 5-10 year horizon.” (p. 2).
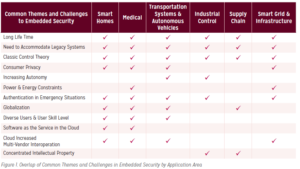
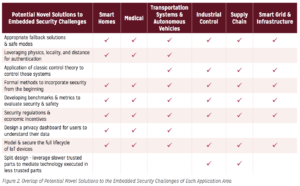
“The workshop breakout presentations revealed that there were numerous common themes in terms of trends, challenges, and solutions that impacted most or all of the five applications areas. However, there were also some important distinctions between the areas. For example, increased connectivity leads to increased attack surfaces in all five areas, however network-based defenses vary considerably depending on the threat models and impacts on performance and utility. As another example, machine learning algorithms and the move towards autonomous systems are particularly significant in all areas, especially for detecting intrusion and anomalous behavior, however specific vulnerabilities vary depending on the area. Furthermore, the requirements (performance, cost, reliability, life-time, etc.) for each area are significantly different, thus leading to different challenges, and warranting different approaches to security and privacy. Figure 1 shows the overlap of common trends and challenges by application area as well as notable areas of distinction, while Figure 2 shows areas of overlapping, potential novel solutions for these challenges.” (p. 11).
To learn more about the research recommendations that emerged at the workshop, read the full report here.








